I. General
1. Objetives.
This project intends to provide an enterprise class high available statefull firewall system (HA Firewall system) build with open source software (available for free on Internet).
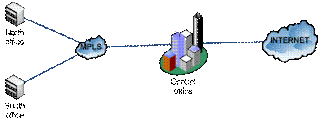
The HAF Corporation has a web application and a mail server on internet and 2 internal servers (on central office) and 2 remote offices (south and north) connected over an MPLS network.
This project don´t intend cover other HA components of the network (switchs, routers, links, etc.), just firewall HA.
This project doesn’t intend explain all options of each software component used nor substitute the fwbuilder manual, just the options used (how and why). It presents how to configure a particular HA firewall system step by step. References for where to find in depth information are provided.
Some information about what can be done to expand or adapt this firewall system is provided.
The main goal is to show how all components work together.
This material is provided "as is", with absolutely no warranty expressed or implied. Any use is at your own risk. The information in this document is subject to change without notice. I assume no responsibility or liability for any errors or inaccuracies that may appear in this material.
2. Overview.
This firewall system is composed of tree Linux boxes.
The first (fw-console) to create and maintain the firewall database (objects, policy, routes, etc) with a GUI (fwbuilder). It compiles and installs “iptables-script” on the “walls”. This host also will provide time synchronization (ntpd) and log consolidation (syslogd).
*fwbuilder can manage a lot of firewalls (clustered or not) from a centralized firewall database. For in-depth information about what can be done and how to use fwbuilder look at http://fwbuilder.org. There is a really good documentation.
*Other useful thinks, like monitoring (http://www.nagios.org, http://www.mrtg.org, http://www.cacti.net) can be installed in this host too.
The others (fw-01 and fw-02) are “walls” (cluster nodes). node-1 (fw-01) is the “master-node” that manages the traffic. Heartbeat automatic transfers the traffic to the node-2 (fw-02) if fw-01 fails. Conntrackd replicates conntrack table between the nodes, so active sessions are not “broke” when traffic is switched from one node to other.
*I have used heartbeat for the last 10 year on many HA projects (web servers, application servers, database servers, etc).
*contrackd is really new for me, but it seems to work fine.
*Other useful things, like VPN (http://www.poptop.org, http://www.openswan.org), traffic analyzers (http://www.ntop.org) and IDS (http://www.snort.org) can be installed on dose hosts too.
*One alternative is to have a traffic managed for node-1 node and VPN for node-2. If one node fails, the other does both work (2 services with different masters on heartbeat).
Those hosts live on a “dark & cold” datacenter far away, so a PC (pc-01) in the office will be use to administrate the firewall system.
3. Requirements.
Knowledge of Linux administration, networking and firewalls concepts.
Read the fwbuilder user's guide or some background with fwbuilder.
4. Software.
This solution use:
Iptables 1.3.5 (embedded on CentOS) (that manage filters)
Heartbeat 2.1.3 (embedded on CentOS) (that manage services between nodes)
A well-know, stable, robust and flexible Linux distro, based on RedHat Enterprise Linux. Has a lot of documentation and skilled administrators.
An excellent GUI for managing firewalls.
To replicate conntracks between nodes.
5. Hardware.
Is recommended use high quality server with RAID disks, multiple NICs, enough RAM and CPU.
*Requirements of RAM, disk space, NICs and CPU can be very different from one environment to another.
*2x 140GB disks (RAID1), 4x Gbit NICs, 1GB RAM and Xeon Dual Core based server may be a good starting point. A much smaller configuration may work on several environments.
*Each wall can work with just one NIC (using Vlans), but is not recommended. A minimal of two NICs (using Bond and Vlan) can work fine on low traffic environments.
*This configuration was tested on 3 XEN virtual machines (5GB disk, 700MB RAM each) and 4 Vlans over one physical NIC.
6. Network.
Each firewall-node of this project is connected on 4 networks
Inside – the internal lan (where our users work)
Outside – the Internet (where de “evil” lives)
DMZ – the service lan (where our public servers lives)
Sync – an firewall private lan (for node synchronizations)
The firewall system needs, at least, 3 different IP address for each network. Node-1 IP, node-2 IP and clustered IP.
*Clustered IP (generally know as Virtual IP) is the gateway for this network and is moved from one firewall-node heartbeat.
*Many clustered IP can be used for many one-to-one or one-to-many different NATs.
The “sync” network (a private and dedicated network) don´t needs a clustered IP cause is just used for data synchronization between nodes.
*Four Vlans on one or more interconnected switches may be a good starting point.
*bond (port channels / ether channels) combining 2 or more physical eth interfaces can be used to take more throughput and/or availability. Bondx is used instead of ethx on configuration.
*802.11q (trunk) over physical (eth) or aggregated (bond) interfeces can be used share physical connection for many Vlans. Ethx.y or bondx.y is used instead of ethx on configuration.
host | IP addr | def-gw | |||
inside | outside | dmz | sync | ||
gw-01 | 200.201.202.1/28 | ||||
fw-01 | 192.168.100.11/24 | 200.201.202.11/28 | 192.168.150.11/24 | 192.168.255.11/24 | 200.201.202.1/28 |
fw-02 | 192.168.100.12/24 | 200.201.202.12/28 | 192.168.150.12/24 | 192.168.255.12/24 | 200.201.202.1/28 |
fw-cluster | 192.168.100.10/24 | 200.201.202.10/28 | 192.168.150.10/24 | ||
mail-01 | 192.168.150.21/24 | 192.168.150.10/24 | |||
web-01 | 192.168.150.22/24 | 192.168.150.10/24 | |||
pc-01 | 192.168.100.120/24 | 192.168.100.10/24 | |||
fw-console | 192.168.100.13/24 | 192.168.100.10/24 | |||
dns-01 | 192.168.100.31/24 | 192.168.100.10/24 | |||
db-01 | 192.168.100.32/24 | 192.168.100.10/24 | |||
gw-02 | 192.168.100.1/24 | 192.168.100.10/24 | |||
gw-03 | 192.168.101.1/24 | ||||
gw-04 | 192.168.102.1/24 | ||||



No comments:
Post a Comment